Time is of the essence when there is a medical emergency or a criminal investigation. There is a “golden hour” at the onset of an incident when well-thought-out planning and effective response can make or break the situation.
Very much like in medical trauma care or criminal investigations, there is a “golden hour” of IT asset disposition (ITAD) when well thought out planning and effective response can keep an incident from becoming a costly disaster.
The earliest stage of any incident is the most important one to get right. Given the certainty that retired assets go missing, it makes sense to consider the possible scenarios now and figure out how to deal with them before they actually happen.
Prevention is key
An ounce of prevention is worth millions in cure. Bad ITAD increases risks and is a recipe for disaster. Previous posts discuss effective ways to avoid problems associated with bad ITAD.
Unfortunately, losses are a fact of any system – even the most reliable systems. Airlines mishandle 1-in-155 bags. Freight companies lose shipments. FedEx loses packages.
Simple and effective steps can eliminate the vast majority of potential problems. For example, companies that use disposal tags are able to account for 98.4% of their assets – a significant improvement over an average of 78% when companies that only use serial numbers to track IT assets.
We must recognize and mitigate the risks and be prepared to respond when an event inevitably occurs.
Prevention is ideal, but detection is a must
One of the key mottos of information security is, “prevention is ideal, but detection is a must.”
The only way to detect if a retired asset is missing is to reconcile inventories. Manually manipulating spreadsheets can take hours, even days. Purpose-built tools, however, can reconcile inventories in minutes.
Without adequate controls, security incidents can go undetected. There are two basic types of internal controls: preventive and detective. A lock on a door is an example of preventive control. An alarm system on the door would be considered a detective control.
With detective controls, it is important to ensure duties and responsibility are appropriately separated – you don’t want to trust a fox to watch the hen house! Coca-Cola learned this the hard way when it was revealed that 55 stolen laptops were taken over a six-year period by an employee who happened to be responsible for the disposal of the equipment.
Don’t wing it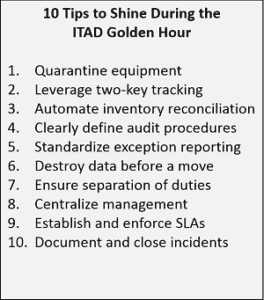
Effective communication is key when time is of the essence. Having clearly defined audit procedures will ensure everyone is on the same page and communicating effectively.
Make sure all involved understand and use specific terminology. Develop and systematize standard exception reporting.
Centralized management allows for control and visibility of the ITAD management function without hampering local disposal activities. It is also the critical coordination point for an effective response during the Golden Hour.
Buy yourself time
ITAD is a business of volume. ITAD vendors focus on efficiently receiving and processing equipment to maximize throughput. As a result, vendors do not like to hold equipment for extended periods of time.
Nearly all missing items, however, can be ‘found’ by having your ITAD vendor reinspect and re-inventory equipment. In order to resolve incidents, it is essential to have your ITAD vendor receive, inventory, and hold equipment until you have fully signed off on everything.
Once the equipment is processed, you will not have an opportunity to have items inspected or re-inventoried. Do not allow equipment to be processed without your approval.
ITAD vendors do not like to quarantine equipment which is why you should establish and enforce SLAs that require vendors to hold equipment for at least 48 hours. Include financial penalties in your contracts that require ITAD vendors to pay if they don’t perform.
Plan ahead
Mike Tyson famously quipped, “Everyone has a plan until they get punched in the mouth.” Even the best laid ITAD plans often go awry, but organizations with effective ITAD programs don’t get knocked out when they do.
The only way to be 100% certain that an ITAD incident never escalates into a breach is to destroy data before a move, and obtain/maintain verifiable documentation.
Assess and improve
Unfortunately, incidents are a reality of any system. Despite our best efforts, events occur that demonstrate vulnerabilities in the system.
Airlines document and scrutinize ‘near-misses’ to help avoid future crashes. Likewise, quantifying the frequency and cause of ITAD incidents can help your company develop strategies to reduce future occurrences. Having accurate and reliable data can also justify the resources needed to run an effective program.
Manage expectations
Getting buy-in from sponsors is essential to creating an effective ITAD program. Ongoing communication is key to maintaining success.
Executives become blind to threats when they never hear about incidents. IT asset management (ITAM) must set realistic expectations and continuously communicate with management to maintain momentum.
Companies cannot rely on informal efforts to communicate ITAD program results to management. Accurate and complete ITAD reporting is the primary way for ITAM to educate executives. Routine tracking reports provide a realistic view for executives to see the challenges that ITAM must overcome to be successful.
Be prepared
Being prepared for the “golden hour” of medical trauma can save hundreds of lives. Not being prepared for the “golden hour” of a criminal investigation might result in someone getting away with murder.
Having the ability to recognize the “golden hour” of ITAD and being prepared to respond effectively will not save lives or solve crimes, but recognizing the situation and responding swiftly will save your company from expensive judgments and fines.
Resources
This post was shared on the Retire-IT blog. Read similar posts and subscribe above.
Retire-IT is committed to promoting effective ITAD. For additional information and resources, please visit www.Retire-IT.com.
Call (888) 839-6555 to talk about how we can support you.



