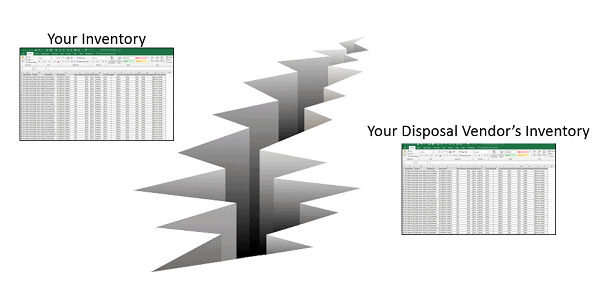
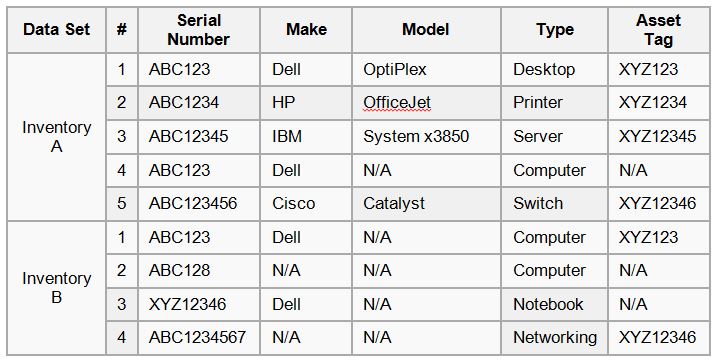
Traditional ITAD vendors can undervalue equipment & lack transparency. Learn how ITAD consultants offer a secure, cost-effective solution with maximized value recovery.
Welcome to the ITAD Aficionado blog!
This is a collection of comments, rants, musings, and links to articles of interest for anyone serious about ITAD.
The views expressed are opinions of individuals and not necessarily those of Retire-IT (unless, of course, they make a lot of sense and then we would like to take some credit).